Amplification Hell: Abusing Network Protocols for DDoS
|
In amplification DDoS attacks, an adversary aims to exhaust the victim's bandwidth. He abuses the fact that public servers of UDP-based network protocols respond to requests without further validating the identity (i.e., the IP address) of the sender. Amplification attacks are attractive for adversaries: (i) He disguises his identity, as victims receive backscatter traffic from amplifiers, i.e., systems that can be abused to send traffic to the victim on the attacker's behalf; (ii) The simultaneous abuse of multiple amplifiers permits a highly-distributed DoS attack to be con- ducted from a single Internet uplink. (iii) The traffic reflected to the victim is significantly larger in bandwidth than the traffic an attacker has to send to the amplifiers. 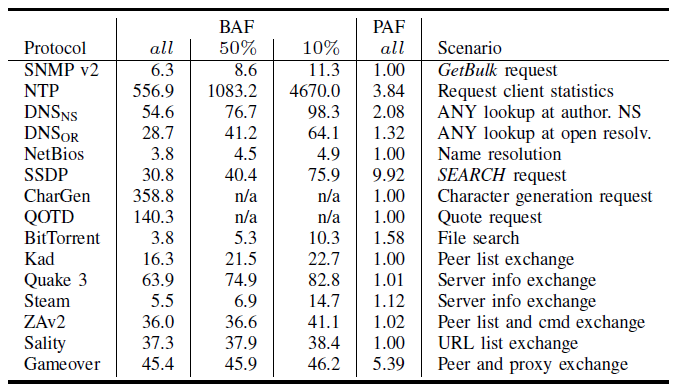
The table above gives an overview of amplification rates that an attacker can achieve by abusing the protocols. The bandwidth amplification factor (BAF) computes the bandwidth multiplier in terms of number of UDP payload bytes that an amplifier sends to answer a request, compared to the number of UDP payload bytes of the request. The packet amplification factor (PAF) is the packet multiplier in terms of number of IP packets that an amplifier sends to answer a request. A few protocols, like NTP, stand out. Therefore, we (that is, the security community) currently aim to fix the most severe amplification vulnerabilities. 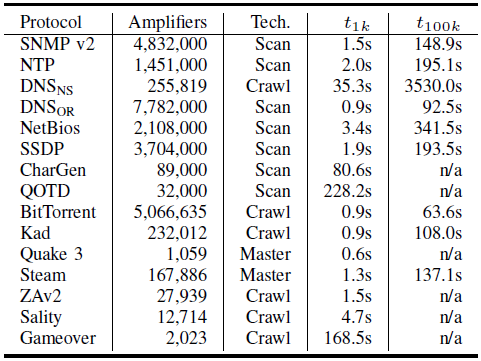
The second table shows how many amplifiers I extrapolated from a smaller scan. Note that these numbers do not necessarily reflect the total number of open systems per protocol - again, I focused on the most severe systems. For example, for NTP, I counted only the servers that support the monlist request type. Similarly, for DNS, I counted servers that support EDNS0. As such, the total numbers of server is higher. Wondering about possible countermeasures? This is what we can do:
Christian
References (my interviews or advisories that I reported):
|

